Componente OAuth 2.0 de 3 Patas
Descripción general
Se requiere el componente OAuth 2.0 (3LO) de tres patas para admitir 3LO en un conector. Permite el uso de autenticación 3LO con aplicaciones (nube y privada) registrado en Harmony. Para obtener más información sobre 3LO, consulte Conector OAuth 2.0 de 3 patas.
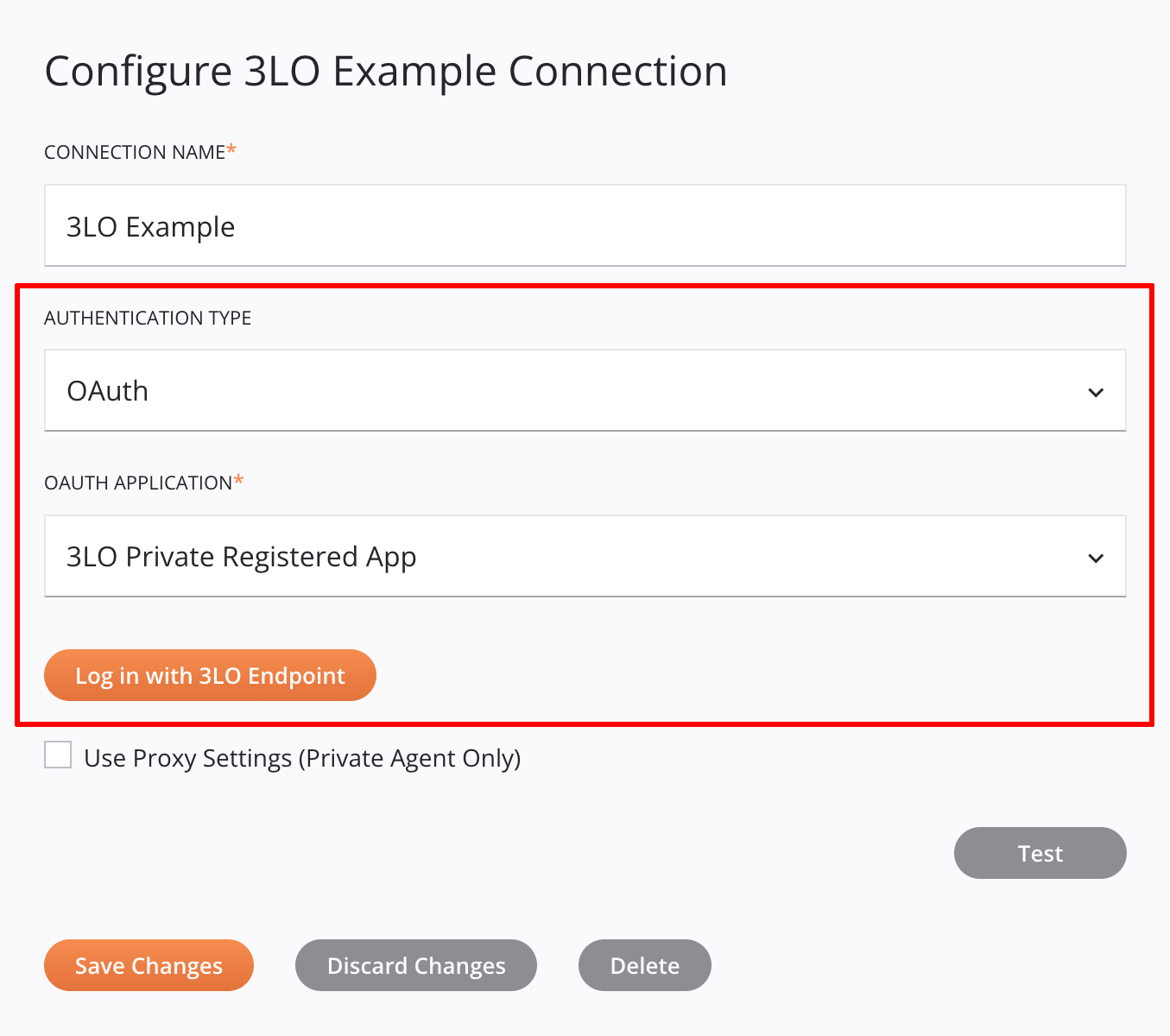
El componente 3LO está diseñado para la configuración del extremo del conector y debe agregarse al endpoint en el adapter.json solo. Cuando se implementa, así es como aparece el componente 3LO cuando los elementos asociados son visibles:
Importante
Si utiliza un Agente Privado, los conectores habilitados para 3LO requieren la versión del agente 10.83/11.21 o posterior.
Características de los componentes
El componente 3LO incluye definiciones para tipos de autenticación y un botón de inicio de sesión:
-
Menú desplegable Tipo de autenticación: Los usuarios seleccionan de una lista de tipos de autenticación definidos por el desarrollador. Como mínimo, un
enumValuesdefinición con1como surealValuese requiere.1siempre representará la autenticación 3LO.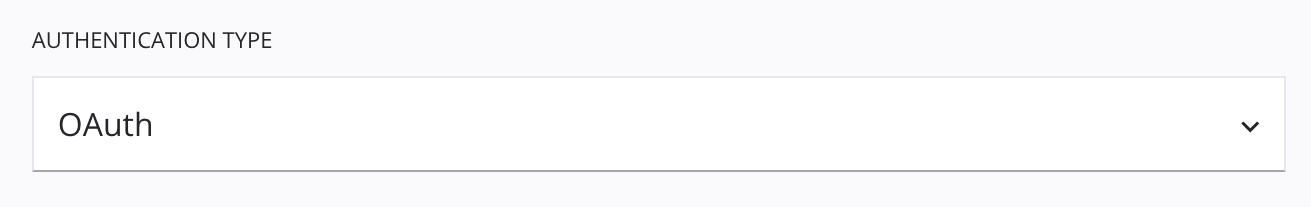
-
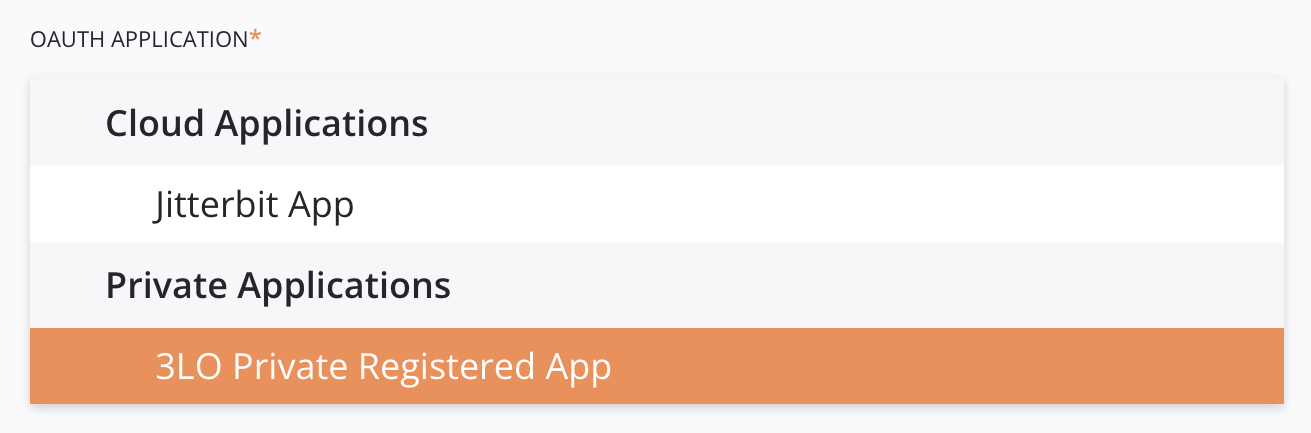
Menú desplegable de aplicaciones OAuth: Los usuarios seleccionan de una lista de Aplicaciones en la nube y Aplicaciones privadas asociadas generadas por Integration Studio. Este elemento de la interfaz de usuario se mostrará en Integration Studio cuando haya una aplicación privada asociada con el conector habilitado para 3LO. Este es el menú desplegable cuando está visible y expandido:
Importante
Aplicaciones privadas se puede definir y modificar libremente en Management Console Registros de aplicaciones página. Los socios de Jitterbit pueden configurar aplicaciones en la nube trabajando directamente con Jitterbit.
-
Botón de inicio de sesión: Los usuarios hacen clic para autenticarse con un proveedor externo de OAuth.

Componente JSON
El componente 3LO se implementa agregando dos propiedades al endpoint en el adapter.json. Ambos son necesarios para que 3LO funcione como se espera con un conector.
{
"name": "3lo_auth_type", // Required
"displayName": "{{Para ser reemplazado}}", // Authentication Type dropdown name
"enumValues": [
{
"enumValue": "3LO",
"realValue": "1" // Required
}
]
}
{
"name": "oauth_login", // Required
"displayName": "Log in with {{Para ser reemplazado}}", // Login button name
"widgetHint": "component:oauth-login", // Required
}
Consejo
Si 3LO es el único tipo de autenticación planificado para el conector, puede ocultar el menú desplegable en la interfaz de usuario usando hidden mientras defaultValue es 1:
{
"name": "3lo_auth_type",
"hidden": true,
"displayName": "Authentication Type",
"enumValues": [
{
"enumValue": "3LO",
"realValue": "1"
}
],
"defaultValue": "1"
}
Para definir tipos de autenticación adicionales más allá de 3LO, proporciónelos como adicionales enumValues definiciones que comienzan con 2 para realValue:
{
"name": "3lo_auth_type",
"displayName": "Authentication Type",
"enumValues": [
{
"enumValue": "Token-based Auth",
"realValue": "2"
},
{
"enumValue": "3LO",
"realValue": "1"
}
],
"defaultValue": "2"
}
Importante
Para que un conector habilitado para 3LO funcione como se espera, una aplicación (nube o privada) debe estar asociado con el conector habilitado para 3LO.
Aplicaciones privadas se puede definir y modificar libremente en Management Console Registros de aplicaciones página. Los socios de Jitterbit pueden configurar aplicaciones en la nube trabajando directamente con Jitterbit.
Valores de los componentes
Durante la configuración del conector y en tiempo de ejecución, el agente inyectará automáticamente access_token como parte de la props (propiedades) de los métodos del Connector SDK.
Por ejemplo, en el ConnectionFactory, el access_token La propiedad será parte de props en el createConnection método:
@Override
public Connection createConnection(Map<String, String> props) {
// The props parameter contains "access_token" as a key-value pair.
}
Manejo de excepciones
Los conectores habilitados para 3LO deben lanzar una ConnectionException excepción si la llamada HTTP usando access_token devuelve un código de estado no autorizado (HttpStatusCode 401).
La excepción hará que el agente actualice el access_token valor y ejecutar un proceso de reintento entre el agente y el conector. Por ejemplo:
Importante
Los conectores no deben manejar manualmente el access_token proceso de actualización porque ya lo maneja el agente.
public void exampleMethod() throws Connection.ConnectionException {
try {
// Method implementation...
} catch (Exception ex) {
throw new Connection.ConnectionException(Param1, Param2, Param3);
}
}
Configuración de registro de aplicaciones
Una vez implementado el conector habilitado para 3LO, se convertirá en una opción desplegable Conector en la Management Console Registros de aplicaciones.
Requisitos previos
Antes de configurar una aplicación con el conector habilitado para 3LO, complete estos requisitos previos:
- Si utiliza un Agente Privado, instale el conector habilitado para 3LO en el agente.
- Cree la aplicación OAuth en el proveedor externo de OAuth correspondiente. Esto proporcionará la información necesaria para los siguientes pasos, como los valores de ID de cliente y Secreto de cliente. Por ejemplo, si estuviera desarrollando un conector Jira, primero deberá crear una aplicación OAuth asociada en Atlassian Portal.
Configuración
Consulte nuestra documentación en Management Console Registros de aplicaciones para proporcionar allí la información relevante para una nueva aplicación privada, incluidas las Opciones avanzadas relevantes según los requisitos o la configuración del proveedor externo elegido.